0-days offered by Austrian agency used to hack Home windows customers, Microsoft says
[ad_1]

Microsoft stated on Wednesday that an Austria-based firm named DSIRF used a number of Home windows and Adobe Reader zero-days to hack organizations positioned in Europe and Central America.
A number of information retailers have revealed articles like this one, which cited marketing materials and different proof linking DSIRF to Subzero, a malicious toolset for “automated exfiltration of delicate/personal information” and “tailor-made entry operations [including] identification, monitoring and infiltration of threats.”
Members of the Microsoft Risk Intelligence Middle, or MSTIC, stated they’ve discovered Subzero malware infections unfold by a wide range of strategies, together with the exploitation of what on the time had been Home windows and Adobe Reader zero-days, that means the attackers knew of the vulnerabilities earlier than Microsoft and Adobe did. Targets of the assaults noticed so far embrace legislation companies, banks, and strategic consultancies in international locations akin to Austria, the UK, and Panama, though these aren’t essentially the international locations wherein the DSIRF clients who paid for the assault resided.
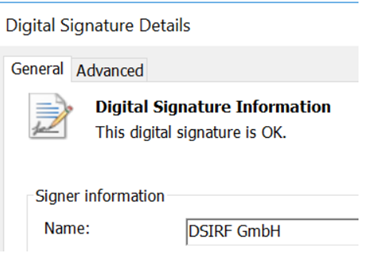
“MSTIC has discovered a number of hyperlinks between DSIRF and the exploits and malware utilized in these assaults,” Microsoft researchers wrote. “These embrace command-and-control infrastructure utilized by the malware straight linking to DSIRF, a DSIRF-associated GitHub account being utilized in one assault, a code signing certificates issued to DSIRF getting used to signal an exploit, and different open supply information experiences attributing Subzero to DSIRF.”
Microsoft
An e-mail despatched to DSIRF in search of remark wasn’t returned.
Wednesday’s submit is the newest to take purpose on the scourge of mercenary spy ware offered by personal firms. Israel-based NSO Group is the best-known instance of a for-profit firm promoting expensive exploits that always compromise the units belonging to journalists, attorneys, and activists. One other Israel-based mercenary named Candiru was profiled by Microsoft and College of Toronto’s Citizen Lab final yr and was not too long ago caught orchestrating phishing campaigns on behalf of shoppers that might bypass two-factor authentication.
Additionally on Wednesday, the US Home of Representatives Everlasting Choose Committee on Intelligence held a listening to on the proliferation of foreign commercial spyware. One of many audio system was the daughter of a former lodge supervisor in Rwanda who was imprisoned after saving tons of of lives and talking out in regards to the genocide that had taken place. She recounted the expertise of getting her cellphone hacked with NSO spyware the identical day she met with the Belgian overseas affairs minister.
Referring to DSIRF utilizing the work KNOTWEED, Microsoft researchers wrote:
In Could 2022, MSTIC discovered an Adobe Reader distant code execution (RCE) and a 0-day Home windows privilege escalation exploit chain being utilized in an assault that led to the deployment of Subzero. The exploits had been packaged right into a PDF doc that was despatched to the sufferer through e-mail. Microsoft was not in a position to purchase the PDF or Adobe Reader RCE portion of the exploit chain, however the sufferer’s Adobe Reader model was launched in January 2022, that means that the exploit used was both a 1-day exploit developed between January and Could, or a 0-day exploit. Primarily based on KNOTWEED’s intensive use of different 0-days, we assess with medium confidence that the Adobe Reader RCE is a 0-day exploit. The Home windows exploit was analyzed by MSRC, discovered to be a 0-day exploit, after which patched in July 2022 as CVE-2022-22047. Apparently, there have been indications within the Home windows exploit code that it was additionally designed for use from Chromium-based browsers, though we’ve seen no proof of browser-based assaults.
The CVE-2022-22047 vulnerability is expounded to a problem with activation context caching within the Consumer Server Run-Time Subsystem (CSRSS) on Home windows. At a excessive stage, the vulnerability may allow an attacker to offer a crafted meeting manifest, which might create a malicious activation context within the activation context cache, for an arbitrary course of. This cached context is used the subsequent time the method spawned.
CVE-2022-22047 was utilized in KNOTWEED associated assaults for privilege escalation. The vulnerability additionally supplied the power to flee sandboxes (with some caveats, as mentioned under) and obtain system-level code execution. The exploit chain begins with writing a malicious DLL to disk from the sandboxed Adobe Reader renderer course of. The CVE-2022-22047 exploit was then used to focus on a system course of by offering an utility manifest with an undocumented attribute that specified the trail of the malicious DLL. Then, when the system course of subsequent spawned, the attribute within the malicious activation context was used, the malicious DLL was loaded from the given path, and system-level code execution was achieved.
Wednesday’s submit additionally supplies detailed indicators of compromise that readers can use to find out if they’ve been focused by DSIRF.
Microsoft used the time period PSOA—brief for private-sector offensive actor—to explain cyber mercenaries like DSIRF. The corporate stated most PSOAs function underneath one or each of two fashions. The primary, access-as-a-service, sells full end-to-end hacking instruments to clients to be used in their very own operations. Within the different mannequin, hack-for-hire, the PSOA carries out the focused operations itself.
“Primarily based on noticed assaults and information experiences, MSTIC believes that KNOTWEED might mix these fashions: they promote the Subzero malware to 3rd events however have additionally been noticed utilizing KNOTWEED-associated infrastructure in some assaults, suggesting extra direct involvement,” Microsoft researchers wrote.
Source link